My blog Admantium is hosted on a cloud server managed with Ansible. This article shows you how to use the cloud computing provider Hetzner for setting up an Nginx server with TLS encryption. We will create the server via the management interface and install Nginx using ansible. Then we will get certificates form Lets Encrypt and configure Nginx to only provide HTTP connections.
Creating Hetzner Cloud Server
Hetzner is a German cloud computing provider. The reason I choose them is because they have good prices and a very usable Web UI. Furthermore, the have an HTTP API, as well as a CLI tool, Go and Python libraries.
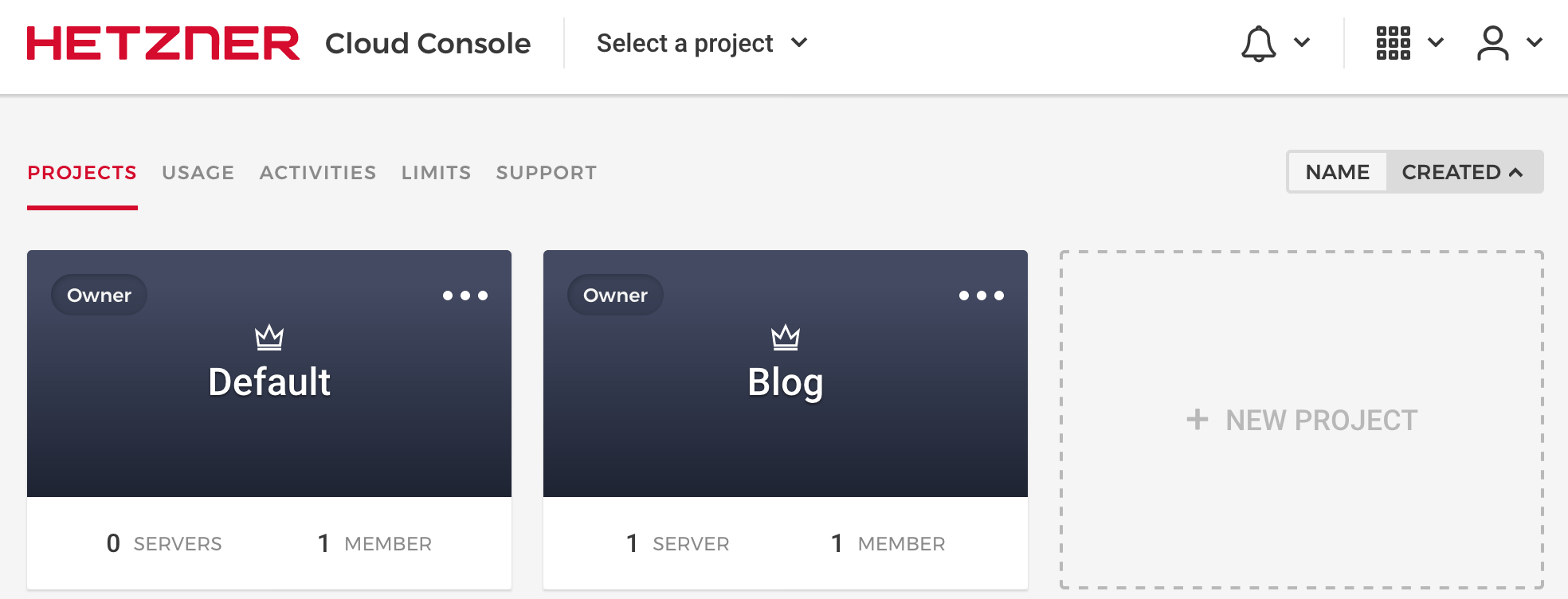
Once you have an account, create a new project.
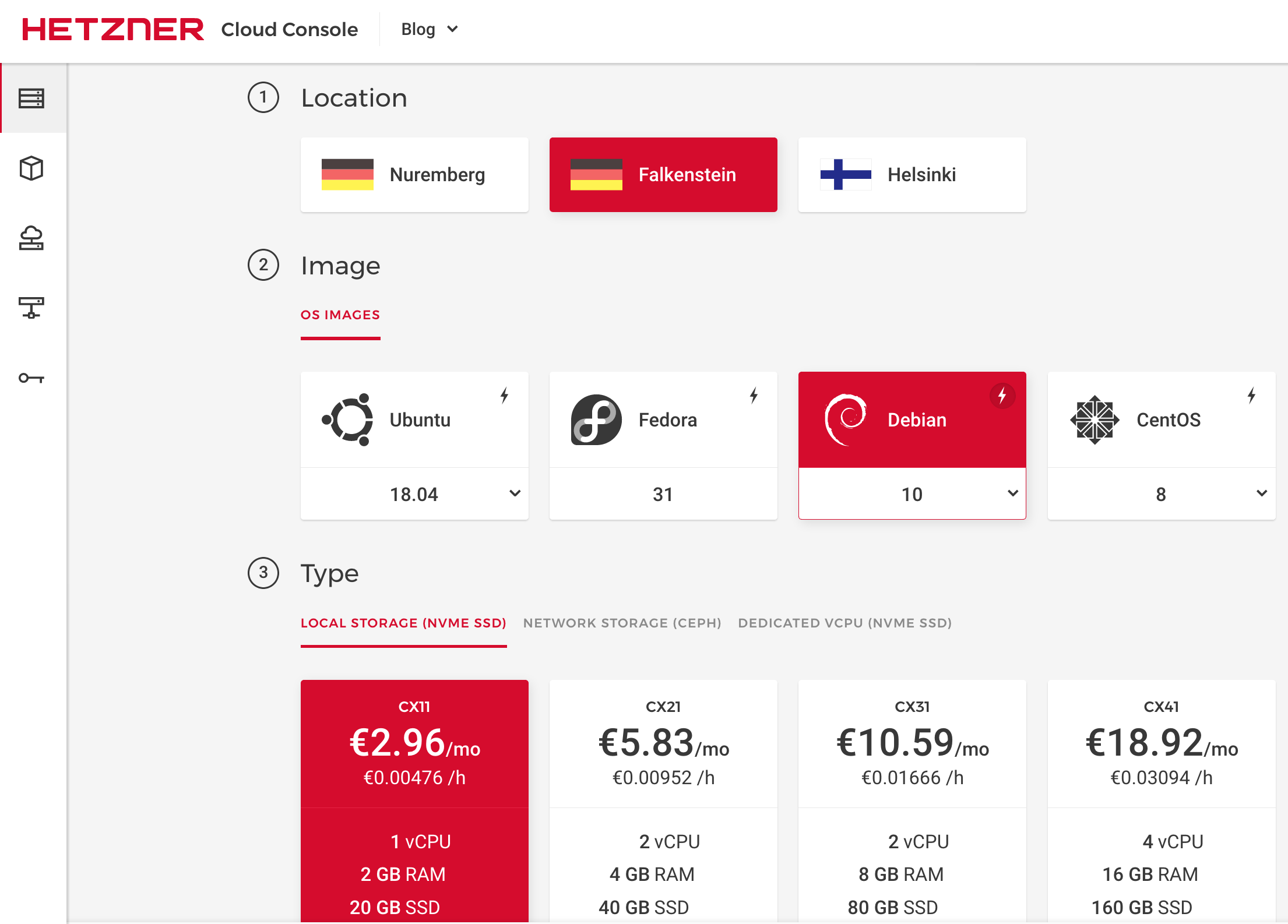
Then add servers. Adding a server means: Decide the location, Linux image and type. Then, optional, add block storage and your SSH public key.
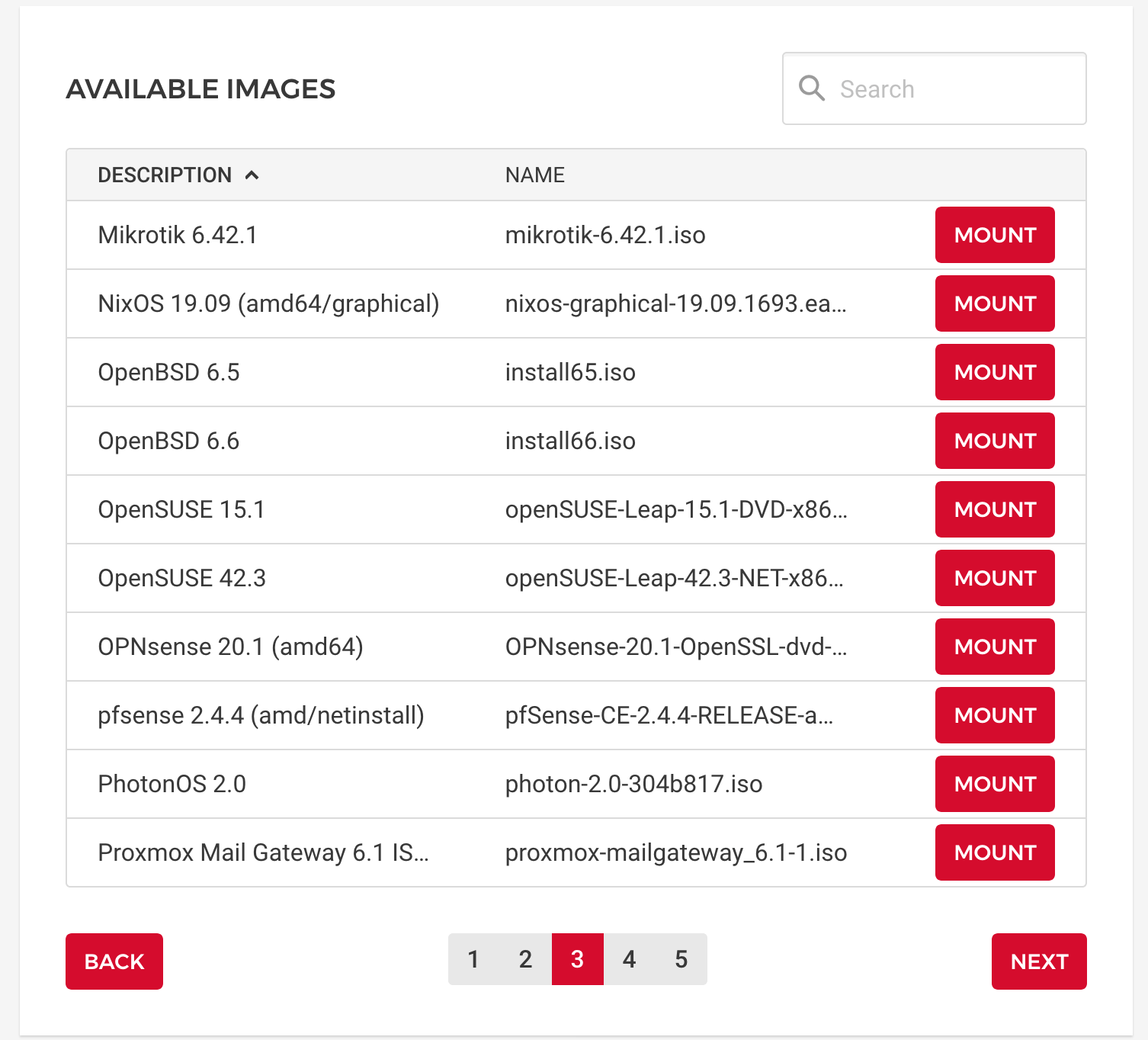
Before the first boot, you only have a limited number of images. But once the server runs, you can choose from a long list of even exotic Linux derivates.
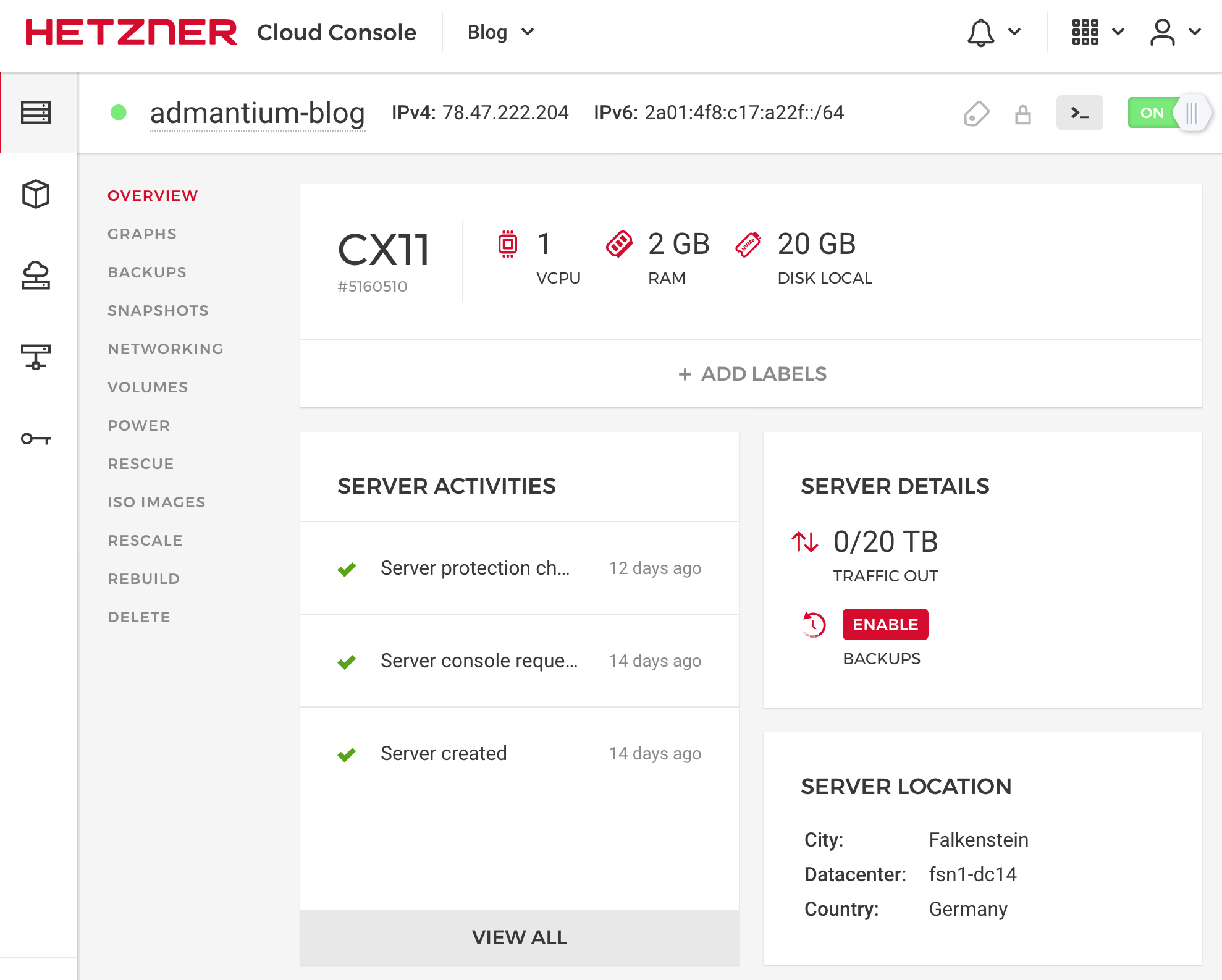
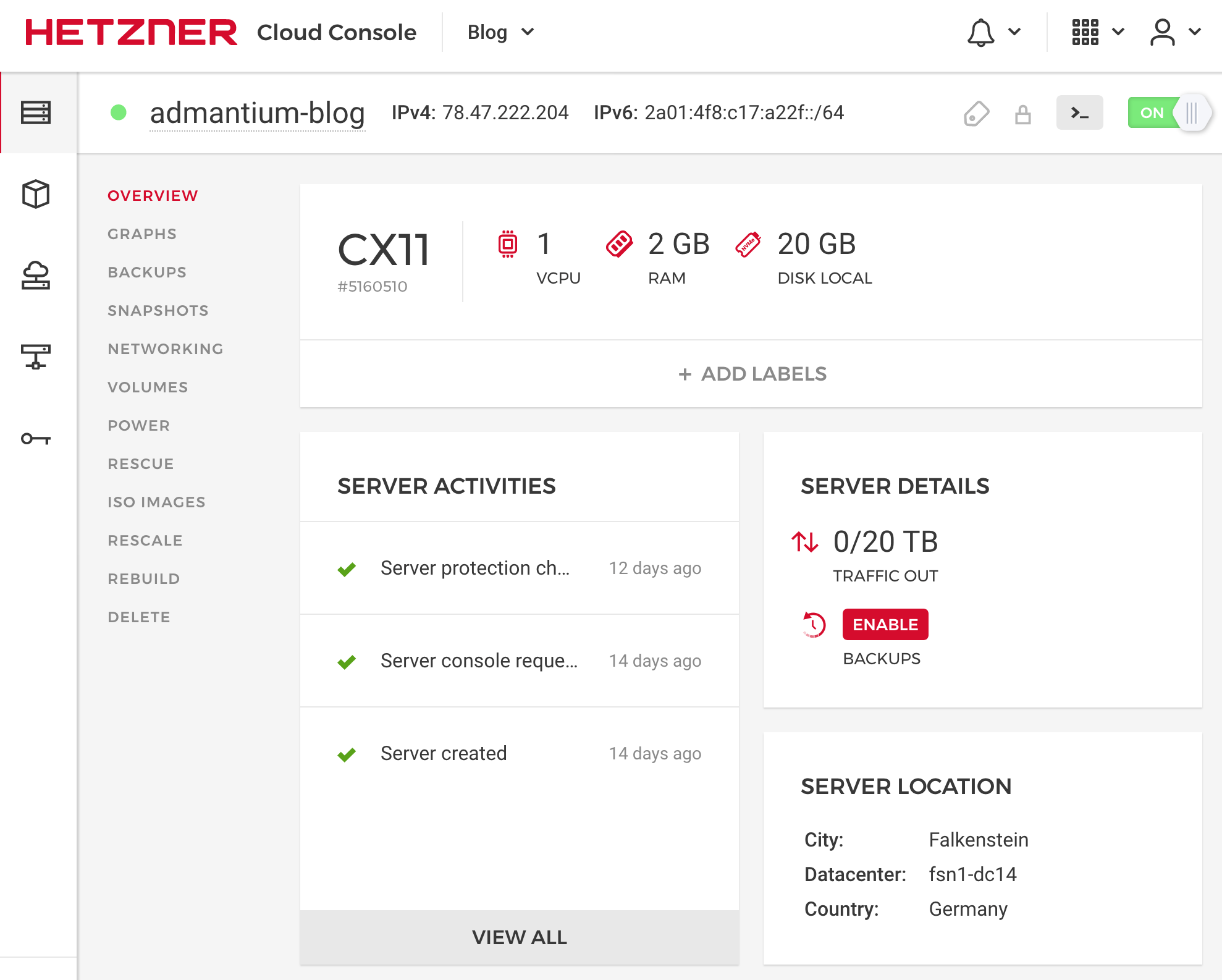
Finally, once your server is running, you can see and configure it in the details view.
Installing Nginx
I install Nginx with the official Ansible role from Nginx. This role gives you great amount of control: Install from OS or compile from sources, customize the nginx.conf, add other sites, and even upload certificates if you already have them. Check the available basic configuration and the upload configuration.
I use this ansible configuration:
- name: Install nginx
gather_facts: true
hosts:
- admantium
tags:
- nginx
become: true
vars:
nginx_install_from: 'os_repository'
nginx_repository: deb https://nginx.org/packages/mainline/debian/ stretch nginx
nginx_main_upload_enable: true
nginx_main_upload_src: config/nginx.conf
nginx_main_upload_dest: /etc/nginx/
nginx_http_upload_enable: true
nginx_http_upload_src: config/http/*.conf
nginx_http_upload_dest: /etc/nginx/conf.d/
roles:
- nginxinc.nginx
The role is executed, Nginx is installed.
Get Certificates with Let’s Encrypt
The installation of valid certificates with Lets Encrypt is nothing short of pleasure: Install and run the certbot program.
apt-get install certbot python-certbot-nginx
certbot certonly --nginx
The script then asks you to automatically customize your Nginx config, or it shows you the paths to the generated certificates. I opted for the latter, and manually inserted it.
server {
server_name admantium.com;
listen 443 ssl http2;
ssl_certificate /etc/letsencrypt/live/admantium.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/admantium.com/privkey.pem;
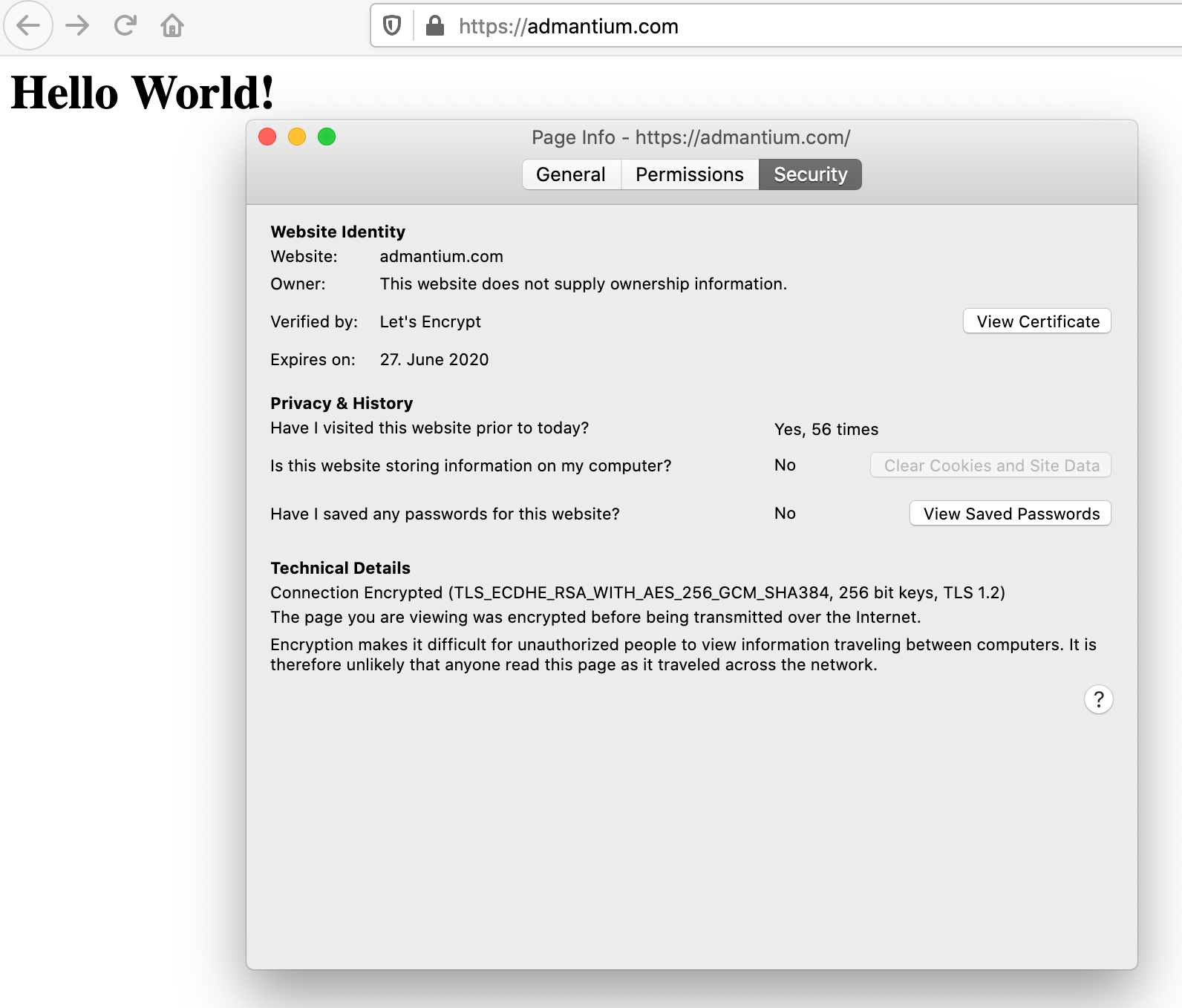
Then I added a simple “Hello World” index page and accessed the server to see the certificate being used in a HTTPS connection.
Securing the Web Server
The final part is to make the TLS connection even more secure. After reading a list of security aspects, I learned the following:
- Only allow
TLSv1.2andTLSv1.3, older version have been compromised - Configure the server to offer a carefully selected set of
ssl_ciphersand tell the client to select one of them - Set the
Strict-Transport-Securityheader, and proper redirects, to only allow TLS connections.
This is achieved with the following config:
##
# SSL Settings
##
ssl_protocols TLSv1.2 TLSv1.3;
ssl_ciphers "ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256";
ssl_prefer_server_ciphers on;
ssl_ecdh_curve secp521r1:secp384r1;
add_header Strict-Transport-Security "max-age=15768000; preload" always;
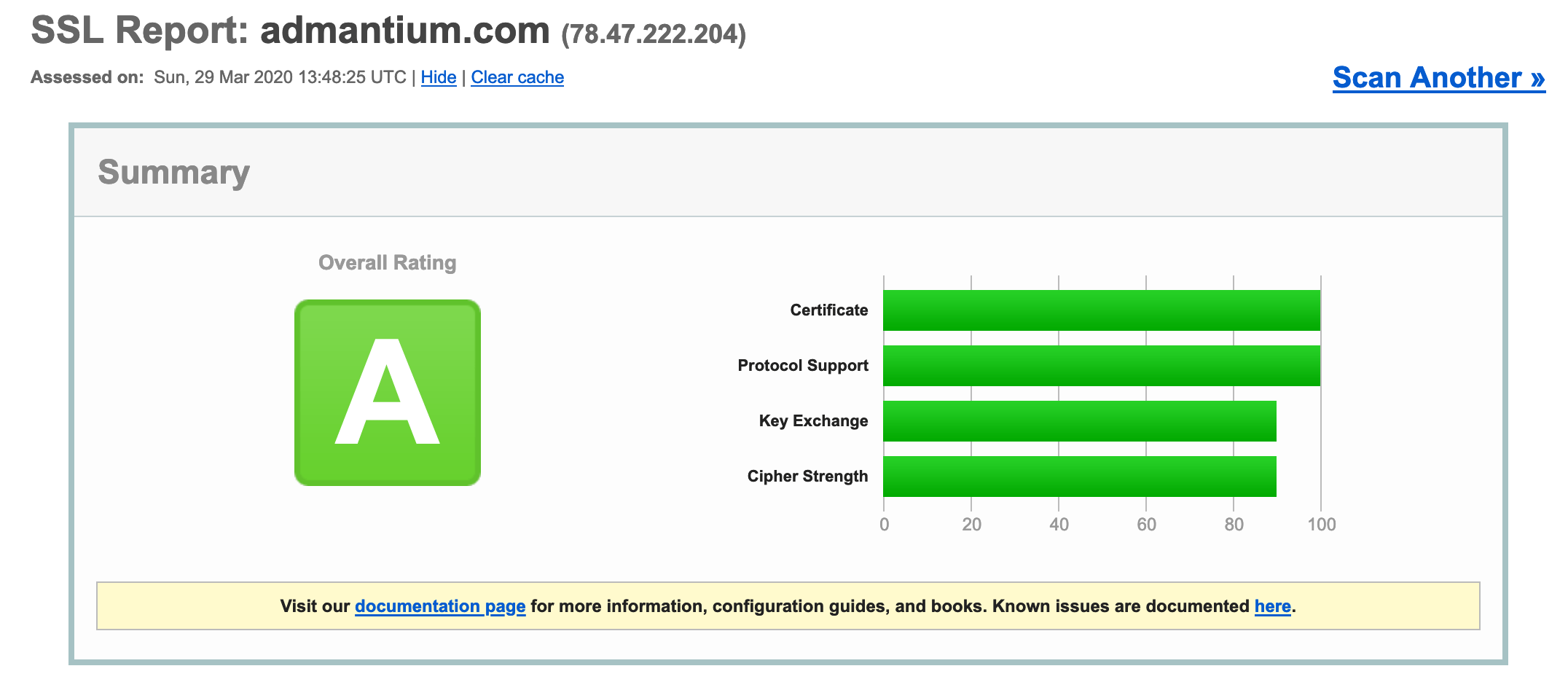
Once in place, I use the SSL labs scanner and could improve the score from C to A. Great result!
Conclusion
This article showed you how to setup a server with the cloud computing provider. You also learned how to apply the official Nginx Ansible role to install and configure the webserver. Finally I showed you how to get certificates with lets encrypt and how to improve your Nginx TLS config.